**This blog post was updated on April 1, 2024.**
Part of growing up is learning about and interacting with aspects of human sexuality. For parents, this can be stressful, confusing, and even scary — but rest assured it’s a normal part of being a kid. Children learn about the world through exploratory play, and that includes exploratory sexual play. Because of this, it’s important for parents to support their kids through every stage in their development, from preschool to high school. Knowing what to generally expect for age-appropriate sexual curiosity will help you gauge where your child is at. In this post, we’ll provide you with guideposts for what’s considered common behaviors for kids in each age range — as well as potential dangers like sexting and grooming.
Stages of Sexual Behavior in Children
Preschool (ages 0–5)
Common behaviors
- Curiosity about bodies and bodily functions, may want to touch or see other people's bodies
- Ask a lot of question about body parts, hygiene, toileting, pregnancy, and birth
- Showing their genitals to others
- Exploring genitals by touch and can experience pleasure
- In their play they may act out what they have seen (kissing, arguing, etc)
Uncommon behaviors
- Knowledge of specific sexual acts or explicit sexual language
- Engaging with other children in adult-like sexual contact
- Sexual behavior that involves children who are 4 or more years apart
- Sexual behaviors that involve coercion
Early school-age (5–9)
Common behaviors
- Full of curiosity and questions
- Peer touching, making dirty jokes (usually not fully understood), and talking with their friends about sexual touching and behaviors
- Begin to experience sexual arousal when touching themselves
- Experiencing inhibition and the need for privacy
- Becoming more aware of sexual preference
Uncommon behaviors
- Adult-like sexual interactions
- Having knowledge of specific sexual acts
- Public display of sexual behaviors (including through the use of technology)
- Sexual behavior that involves children who are 4 or more years apart
- Sexual behavior that involves coercion
Preadolescence (9–12)
Common behaviors
- Will want knowledge on sexual materials, relationships, and sexual behaviors
- Increased interest in sex and begin to experiment with other children their same age
- Puberty can begin as early as age nine
- Comparing genital size and function, “locker room behavior”
- Older children may engage in petting, French kissing, touching or rubbing each other’s bodies, and dry humping
- Continue to touch themselves, though often feel embarrassed and deny they are doing it
Uncommon behaviors
- Sexual behaviors between children of widely different ages or abilities
- An interest toward much younger children (4 years or more)
- Involves threats, force, or aggression
- Has a strong aggressive or anxious emotional reaction toward sexual behaviors
- Behaving sexually in a public place
Adolescence (13–16)
Common behaviors
- Asking questions and needing information on decision making, social relationships, and sexual customs
- Continues to touch themselves in private
- Girls begin menstruation and boys will begin to produce sperm
- Sexual experimentation between children of the same age and gender
- Voyeuristic behaviors
- First sexual intercourse will occur for approximately one third of teens
Uncommon behaviors
- Masturbation in public
- Sexual interest toward much younger children
- Non-consensual sexual behaviors
Important Conversations to Have About Potential Dangers
Online predators
Sexual abuse by online predators is a danger that no parent wants to imagine happening to their child. Because of this, it’s important to educate yourself and your family about what these threats look like. One of the most crucial things you can do is make sure your kid knows they can always come to you for help no matter what’s happened.
Sexting
1 in 4 kids today are sexting — it’s essentially become the new first base for Gen Z. Whether you’ve discovered that your kid is sending nudes or you just want to be ready in case it happens, preparation is everything. One of the best ways to get ahead of this issue is to talk about it and discuss the dangers children may not always think about. Our blog posts about sending nudes and potential legal problems can answer your questions and provide you with support.
Consent
It’s never too early to talk to your kids about the concept of bodily consent — the conversation can always grow more comprehensive as they get older. For example, younger kids can understand not wanting to be tickled or always having to hug Aunt Martha. Older kids, on the other hand, can grasp more serious concepts regarding sexual boundaries. Our consent blog post is filled with conversation starters and advice for navigating this important subject.
Sexual assault
It may be difficult to tell if your child has experienced sexual abuse, but watching out for some potential warning signs can help. If your kid has started wetting the bed again, avoids getting undressed, starts having extreme nightmares, or has new knowledge about sexual topics that aren’t usual for their age, something may be wrong.
How to Respond
If you see your child engaging in sexual behavior respond in a calm manner and ask open-ended questions. Not all sexual behaviors, even uncommon ones, are an indication of abuse. A healthy response by a parent can have positive long-term effects on guiding sexual development and eliminating problem behaviors. Ways to manage the interaction include:
- Redirecting the activity to something appropriate, this also allows you time to find a healthy way to respond
- Find a quiet time to talk to your child and ask open ended questions like: How did you get the idea? Or How did you learn about this? Or How did you feel doing it?
- Educate your children about sexual issues in an age appropriate manner. Talking openly with your child provides them with the knowledge and skills to make good decisions.
- Consider the age and stage development of your child, if the behavior is beyond what is typical, speaking to a child therapist or physician may be of help.
It may feel uncomfortable talking about sex with your children, but a healthy parental response provides education and direction. As you set boundaries for your kids regarding their sexual behavior, the use of resources and information on the stages of sexual development are key in understanding how to react. Using an online safety service like Bark can help you start a conversation about healthy sexual behaviors. Positive, clear messages about boundaries, privacy, and consent are an important part of creating open communication on your child’s sexual development and experiences.
Resources for Learning More About Age-Appropriate Sexual Curiosity
- Talking With Your Teen About Sex: A CDC guide
- Sexual Slang Terms and Emoji that Parents Need to Know
- National Child Traumatic Stress Network (NCTSN)
- Sex Education: A Mayo Clinic guide
- Common Sexual Concerns for Grade School Kids: From the American Academy of Pediatrics
- Rape, Abuse & Incest National Network (RAINN)

I’m Brandon Hilkert, dad of two and Chief Technology Officer here at Bark. I’ve noticed some misconceptions and rumors online about how Bark Home slows down internet speeds, and I wanted to address them directly.
I use Bark Home to help protect my own kids (6 and 8) and haven’t experienced a noticeable impact on my family’s internet speeds. Like most families, our TVs all stream Netflix and Hulu, and my wife and I are on Zoom calls for much of the day.
Bark Home will affect one small portion of your internet’s speed — namely, upload capability. I’ll get into more detail about what this means below, but generally speaking, most people have a good experience, even with upload speeds under 20 Mbps (upload speeds usually range from 1–15 Mbps).
However, homes that have custom networking setups for very specific uses may be more affected.
Check out the Bark HomeHow Bark Home Works
Bark Home works by telling all the devices connected to your Wi-Fi network that it’s actually your router. This is important because, in order to make decisions about what can be accessed online, the Bark Home needs to be able to handle all of your traffic. It basically says to the devices (phones, TVs, Xboxes): "Hey, I'm the router, check in with me before you allow or block anything."
When you try to access a website or app like Facebook or Instagram, a "request" is sent to facebook.com or instagram.com to access their content. This flows through the Bark Home for a check-in based on the settings you've applied in your Bark dashboard.
While it’s asking Bark if it’s allowed, it’s also asking your internet service provider's DNS for the address of facebook.com. These requests are lightning fast. Often single- or double-digit milliseconds — that’s imperceivable to humans!
If your Bark Home settings allow the request, the request to download content from the website goes out as usual, and at that point, the website’s server will respond straight back to you.
This is important — it means that Bark Home will NEVER affect your download speeds. This allows users to perform the tasks they want on the internet without any negative effects. The majority of a typical consumer’s activity consists of downloads, so upload speed reductions will have no effect on the majority of your online activity.
Understanding Internet Speeds
When you purchase internet service from an internet service provider (ISP), it’s common to choose a plan based on speeds. Most packages include a speed for downloads that is larger than uploads. For example, I pay for 40 Mbps download and 10 Mbps upload. When I run a speed test, these speeds are generally confirmed:
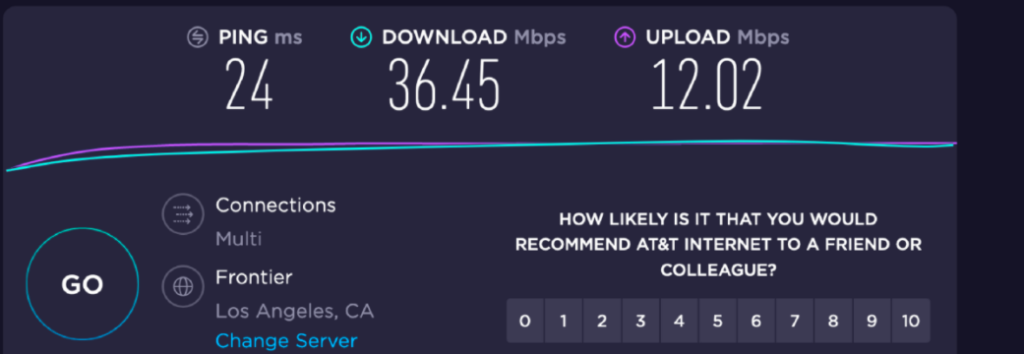
But most folks don’t use all of their bandwidth
However, this isn’t always the case. There have been plenty of times I’ve run a bandwidth test on my home network and only gotten half of what was expected. While that’s disappointing, it’s rare for it to limit my ability to perform common internet tasks — and I’ve worked remotely for Bark for 5 years in an exclusively technical capacity. Plus, if devices in your home are using up some of the total bandwidth available, the speed test will reflect that and return lower numbers than expected.
The average family isn’t uploading much data
The good news is that most consumers don’t need to upload much data at all. The most common uses for uploads would be something like participating in a video chat (you’re uploading your video stream). Even then, a typical Zoom video chat might use up to 3 Mbps. So while my internet is limited to 10 Mbps (as shown in the benchmarks above), a single video stream would consume only 5% of that (based on my ISP speeds — most are significantly faster).
Starting points matter for measuring speed
The speeds I get from my ISP are a little slower compared to the rest of the industry. As a result, my speeds aren’t affected by including Bark Home in my home network. The decrease in upload speeds will be proportional to the total throughput from the ISP. The larger the upload speeds, the more significant of a decrease you’ll see. It’s not unreasonable for 500 Mbps from the ISP to reduce down to 250-300 Mbps with Bark Home connected. While this seems like a lot in proportion, the reality is that it shouldn’t affect everyday use of the internet with any perceptible difference — 250 Mbps is still incredibly fast (and several times faster than my own home internet speed on the best of days).
If these speeds aren’t sufficient for your family, it's likely Bark Home isn’t a good fit for you — you’ll probably need something high-tech and much more expensive to manage your devices. Which is cool! For Bark Home, we focused on designing a piece of hardware that helps keep our customer's kids safe at an affordable price.
Finding the right balance for your family
Even if Bark Home would limit my uploads, the question remains: How important is that? Are slightly faster uploads (again, likely not important to 99.9% of consumers) worth more to you than allowing your children unfettered access to the internet? For me, the answer is no. Bark Home provides the perfect balance of minimal interruption, increased safety for my kids, and an affordable price.
Many factors affect internet speed, and they’re constantly changing
The perception of speed comes in all forms. We can diagnose many of these reasons and in almost all cases, they have nothing to do with Bark. There’s a lot that goes into fast internet at home (Wi-Fi, your router, your ISP, the public internet routers, and even the weather). Wi-Fi plays a big role in the perception of speed. If you’re near the edges of your network’s signal, for example, you’re likely to experience slower speeds.
We’re Here to Help
If Bark Home is significantly slowing down your internet, something likely went wrong somewhere else in your system. Our support team would be happy to dig into the details and help you get the smooth-operating internet you deserve. Just send an email to help@bark.us to set up a time to talk.
**This blog post was updated on December 6, 2022.**
What is grooming? Well, if you’re a parent or guardian, you’ve probably worried about your child getting kidnapped by a predator at a playground or in a mall. But predators can also approach your child without ever being in the same room with them. All they have to do is send a simple message on the internet. Below we will try to answer your question, “What does grooming mean?”
What Is Grooming & How To The Spot Signs of Grooming
Online grooming occurs when a predator initiates and cultivates a relationship with a child through the internet, culminating in sexual abuse that can include:
- Taking sexual photos
- Sending sexual messages
- Sextortion
- In-person sexual abuse
- Trafficking
The process of grooming is a purposefully slow one, as predators methodically take steps to build relationships with children and gain their trust. Predators are masters at manipulation and can appear kind and helpful to hide their ulterior motives, taking advantage of a child’s naivete.
The steps below outline the general pattern of behavior consistent with the signs of grooming. However, every situation is unique, so variations are always possible. Do your best to always be aware of any adult who begins to take an interest in your child, and be sure to check in with your child regularly so they know they can come to you if they ever experience something negative online.
Targeting
Predators often set their sights on vulnerable children, such as those who are emotionally fragile or have less parental oversight. Their first interactions with the child are generally pleasant and include light conversation to lower defenses and make their target feel important. Many predators initiate conversations on public chat apps or in the chat section of games for kids, pretending to be younger than they really are.
Engaging
Many times, the predator will try to fill some sort of need the child has, such as a desire for attention. The adult might also try to connect with their victim by paying them compliments, listening to them, or buying gifts. Be aware of any presents your child may receive from other adults, especially electronic devices, as these may be given for the purpose of becoming a way for the predator to communicate directly with your child.
Boundary Testing
At this point, the predator will attempt to deepen the relationship and gauge the level of threat he’s facing from the parents. He might ask questions to see how closely the child’s devices are monitored and try to figure out whether the child would be believed if they tell their parents about the relationship. During this time, kids may become more secretive about their online activity, so pay attention if their attitude changes when discussing what they do while they’re on their devices.
Isolating
Here, the predator might try to separate the child from their family by establishing himself as the most important person to them. He will try to gain the trust of the child completely, convincing them that they share a special bond. A predator will also look for opportunities to create emotional distance between the child and their family, often using sly tactics to create situations to reinforce the idea of a “special relationship.” Trust your instincts when something isn’t right when it comes to how your child is acting.
Sexualizing
This stage culminates in sexual activity. While some perpetrators might attempt to meet their victims in person, others carry out their sexual abuse entirely online. Predators will begin to discuss sex explicitly, mentioning sexual activities with the child to desensitize them. Some predators have been known to show children pictures of other minors without their clothing in order to make it appear more normal. This influx of sexual information will make the child know far more about sexual activity than is age-appropriate. At this point, the predator may also begin to request sexual videos of their victim and/or send their own.
Controlling
When a predator starts to abuse a child, they will go to great lengths to maintain control and ensure the child is emotionally dependent on them. In most cases, the offender uses secrecy, blame, and even threats of retribution to keep children from saying anything. Let your kids know they can come to you when anyone asks them to do something they are not comfortable with, even if that person is an adult.
What You Can Do When You See Signs of Grooming
So, how do you spot the signs of grooming? Children of any gender, family situation, and socioeconomic status can be targeted as victims of grooming – no one is immune. To help protect your child from online predators, there are a number of steps you can take, including:
- Encouraging your child to be “share aware” by talking openly and often about what sites they’re visiting, games they’re playing, and people they’re chatting with.
- Creating a family environment where your child feels safe talking about difficult topics. The safer a child feels, the more likely they are to open up when something bad happens.
- Monitoring their devices for potentially harmful communications. Bark is designed to detect messages that may be inappropriate or indicative of sexual abuse. Our screen time and web filtering features can also help parents and guardians manage how their child accesses the internet.
Hopefully, we were able to answer your question, “What does grooming mean?” Signs of grooming can be difficult to spot because sexual predators are adept at coercing their victims into keeping quiet. Predators can even befriend parents and caregivers, which makes it even harder to recognize when something is going on. Maintaining an open line of communication with your child and paying extra attention to the amount of time they spend with other adults, as well as monitoring and managing their online activity, can help protect your child from predators.
Above all, make sure your child knows they are not at fault for anything inappropriate an adult says or does to them. You’re there to help and protect them — not punish them for a predator’s actions. When parents know the signs to look for, they’re in a better position to help keep their kids safe both online and in real life.

What does it mean to groom someone? Grooming is the process by which someone befriends and gains the trust of a child (and sometimes the child’s friends and family) in order to take advantage of the child for sexual purposes. Grooming has typically been done in person before the digital age. Today, online grooming has become the main method that sexual predators seek minors.
To accomplish this, predators are masters at manipulation, often appearing kind and helpful. However, there are grooming signs you should be aware of, including the six stages of grooming. These red flags could mean a child is experiencing grooming by an online sexual predator.
*Trigger alert*
Friendship Forming Stage: Targeting and Gaining Trust
The friendship forming stage is composed of conversations in which the predator tries to get introduced to the child. Predators target vulnerable children – those who are needy, unhappy, unable to talk about abuse, or have less parental oversight. Next, the predator will gather information about the child and the child’s family to gain the child’s trust over time. It’s extremely important to be aware of new people in your life and the amount of time they spend with your child and your family. Make sure your child knows that they can talk to you about anything and that you’re there to listen.
Example: Predator exchanges information with the child or parent to get personal contact information, such as email addresses or usernames for social media sites. Additionally, the predator inquires about the relationships in the household.
Relationship Forming Stage: Filling the Child’s (or Family’s) Needs
After gaining access to the child, the predator starts forming a relationship by talking to them about family and school life. Next, the predator fills some sort of need that the child or the family has to ingrain himself into their lives. This may be monetary in nature; for example, a single mother struggling to pay the bills may receive cash or offers to take care of bills.
Predators may also fill a child’s desire for attention by buying them gifts, taking them places, etc. Be aware of any gifts your child may receive from other adults, especially electronic devices. Be extra cautious if someone you haven’t known long offers to help in an overly generous manner.
Example: The predator tries to know more about the interest and hobbies of the child so that they can exploit them. They deceive the child into believing they are in a relationship. At this stage the predator gives soft compliments, calling them “sweetie,” “cutie,” etc.
Risk Assessment Stage: Gauging the Level of Threat
The predator at this stage tries to gauge the level of threat and danger the caregivers pose. They ask questions to see how closely the child is monitored online and in real life. They try to gauge how close the child is to the family and whether their actions will be reported and believed.
In an interview with two child sex offenders, WBIR 10NEWs reported that one of the top deterrents for predators were adults who monitor the electronic communications of the child. Close relationships, close monitoring, and a child who has been warned about predators are huge threats to a predator.
Example: Predators will ask questions like, “Are your parents around?” and “Who else uses the computer?” or “Can you delete your chats?” and “Do your parents monitor your online accounts?”
Exclusivity Stage: Isolating the Child from Others
At this stage, the predator tries to gain the trust of the child completely. The predator asserts that they share a special bond. Often the concept of love and care are introduced.
A predator will look for opportunities to spend time alone with the child. They will often use sly tactics to create these situations and use this time to further reinforce the idea of a special relationship. Trips to amusement parks, offers to tutor your child for free, and other similar situations may signify that your child is being groomed. Trust your instincts should you feel something is amiss.
Examples: Feelings of love and exclusiveness are expressed by the predator. Strong compliments are given. They will say things like, “You are a sweetheart,” or “You are so cute when you look like that,” or “I feel a deep connection with you I don’t feel with anyone else.”
Sexual Stage: Desensitizing the Child
What does it mean to groom someone for the purpose of sex? During the sexual stage, predators ask questions about the child’s sexuality. They will ask things like, “Are you a virgin?” or will talk about masturbation. Some pedophiles talk in great depth about sexual activities with the child to desensitize them to the language and content. They do this to prepare the child for actual physical interaction..
Predators have been known to show children pictures of other children without their clothing in order to make it appear “normal” and “natural.” Some even take the child swimming naked together in an effort to play to the child’s natural curiosity. The predator may introduce porn videos. For this reason, it is important to maintain an open line of communication with your children and act on anything that doesn’t seem typical age-appropriate sexual curiosity.
Examples: The predator gives sexual-oriented compliments, exchanges sexualized pictures, and gives body and figure descriptions. They will say things like, “you are sexy,” ask the child to be their boyfriend or girlfriend, or ask for nudes and sexual text messages.
Conclusion Stage: Controlling the Child and Situation
The conclusion stage occurs when the pedophile begins the physical abuse. Once it begins, they will go to great lengths to maintain control. In most cases, the offender uses secrecy, blame, and even threats to keep the child from saying anything.
The predator’s goal is to maintain the child’s participation, all while hiding it from everyone else. If your child appears withdrawn and sullen, or if they appear fearful and depressed when it’s time to see a particular person, this may be a sign that they’ve been conditioned to remain silent about activities with this person. Let your children know they can come to you when anyone asks them to do something they are not comfortable with — even if that person is an adult.
Examples: A predator will ask questions in this stage like, “Are you able to meet up with me alone or do your parents always have to know everything?” or “Can you sneak out of your house and meet up at a McDonald’s for a treat” or “When we meet I can’t wait to hug you and kiss you” or “Can you walk to our meeting place or is there a place away from your house I can pick you up in my car?” Questions like this ensure the child comes alone and the predator controls how they meet.
Grooming Signs of an Online Sexual Predator
There are a number of signs to be aware of that may suggest online grooming is taking place. Although some may seem like typical teen behavior, it’s still important to watch out for:
- Wanting or asking to spend more time on the internet
- Being secretive about the sites they visit or who they are talking to online
- Switching screens when you come near them when they are on their computer or phone
- Possessing new items you haven’t given them, especially electronic devices
- Using sexual language you wouldn’t expect them to know or that is not age-appropriate
- Emotions that become more volatile
An informative study by the Indraprastha Institute of Information Technology found that a predator does not necessarily move sequentially through the stages. They also discovered that the relationship forming stage is the most dominant online grooming stage. In other words, more than one stage can be in process at once, and predators do not necessarily go in any particular order.
The truth is grooming signs can be difficult to spot. This is because sexual predators tend also to befriend parents and caregivers. Maintaining an open line of communication with your child and paying extra attention to the amount of time they spend with other adults, as well as with Bark, can help protect your child from online sexual predators. Learn more information like “what does it mean to groom someone” and more with Bark today.
**This post was updated on Nov. 21, 2018. This article concentrates on in-person grooming, but learn about signs of online grooming here. **
**This blog post was updated December 7, 2023.**
Whether your child inherited one of your pre-loved iPhones or has the latest release with all the new bells and whistles, it’s important that you help keep them safe while they’re texting, playing games, and surfing the web.
In this guide, we’ll explain how to put parental controls on iPhone devices like screen time limits, web filters, privacy settings, and more. Apple Screen Time and Bark are our two preferred options because Apple Screen Time comes built-in and is free, and Bark because we built it to be completely customizable for parents — and hey, it’s us!
How to Put Parental Controls on iPhone Devices Using Apple’s Built-in Features
To get the most out of Apple’s parental controls, we recommend updating to OS 15, which is supported on most iPhone models, including:
- iPhone 13, iPhone 13 Pro, iPhone SE (3rd gen)
- iPhone 12, iPhone 12 Pro
- iPhone 11, 11 Pro, 11 Pro Max
- iPhone XS and XS Max
- iPhone XR
- iPhone 8 and 8 Plus
- iPhone 7 and 7 Plus
- iPhone 6s and 6s Plus
- iPhone SE
Not sure which OS your child’s device is running? Navigate to Settings > General > Software Update to find out. If the phone is due for an upgrade, you’ll be prompted to download and install the latest software.
Family Sharing
In order to use Apple’s parental controls, you’ll need to have a child account set up. (If your child is already set up, feel free to skip this step). To do this, you’ll need to enable Family Sharing. Family Sharing allows you to share controls for purchases, storage, locations, calendars, and more with members of your family. Simply select features to share and send invitations. You’ll be able to add up to 6 children with Family Sharing, although you won’t be able to add children that are 18 years or older.
To begin, head to the Settings app on your device (iPhone or iPad). From there, tap the Apple ID button, and then tap Set Up Family Sharing > Get Started. From here, you can select apps and features to share across your family’s iCloud account. You’ll be able to customize settings for tons of features, including:
- iTunes and App Store purchases
- Apple Music
- iCloud Storage
- Location Sharing
- Screen Time
Whether your child inherited one of your pre-loved iPhones or has the latest release with all the new bells and whistles, it’s important that you help keep them safe while they’re texting, playing games, and surfing the web.
In this guide, we’ll explain how to put parental controls on iPhone devices like screen time limits, web filters, privacy settings, and more. Apple Screen Time and Bark are our two preferred options because Apple Screen Time comes built-in and is free, and Bark because we built it to be completely customizable for parents — and hey, it’s us!
How to Put Parental Controls on iPhone Devices Using Apple’s Built-in Features
To get the most out of Apple’s parental controls, we recommend updating to OS 15, which is supported on most iPhone models, including:
- iPhone 13, iPhone 13 Pro, iPhone SE (3rd gen)
- iPhone 12, iPhone 12 Pro
- iPhone 11, 11 Pro, 11 Pro Max
- iPhone XS and XS Max
- iPhone XR
- iPhone 8 and 8 Plus
- iPhone 7 and 7 Plus
- iPhone 6s and 6s Plus
- iPhone SE
Not sure which OS your child’s device is running? Navigate to Settings > General > Software Update to find out. If the phone is due for an upgrade, you’ll be prompted to download and install the latest software.
Family Sharing
In order to use Apple’s parental controls, you’ll need to have a child account set up. (If your child is already set up, feel free to skip this step). To do this, you’ll need to enable Family Sharing. Family Sharing allows you to share controls for purchases, storage, locations, calendars, and more with members of your family. Simply select features to share and send invitations. You’ll be able to add up to 6 children with Family Sharing, although you won’t be able to add children that are 18 years or older.
To begin, head to the Settings app on your device (iPhone or iPad). From there, tap the Apple ID button, and then tap Set Up Family Sharing > Get Started. From here, you can select apps and features to share across your family’s iCloud account. You’ll be able to customize settings for tons of features, including:
- iTunes and App Store purchases
- Apple Music
- iCloud Storage
- Location Sharing
- Screen Time
Enabling Screen Time
Apple Screen Time allows you to see how much time your children spend on apps, websites, and more. Additionally, you can set screen time limits, block or limit certain apps and features, restrict explicit content, and prevent purchases and downloads on your child’s device.
Setting Down Time and App Limits
Downtime allows you to decide how long your child can use their phone each day. Use the Start and End times to set a schedule regulating your child’s screen time, then tap Set Downtime.
App Limits allow you to set up time limits on the apps your child uses. Note that you’ll only be able to restrict apps based on pre-selected categories chosen by Apple, which are:
- All Apps & Categories
- Social Networking
- Games
- Entertainment
- Creativity
- Productivity
- Education
- Reading & Reference
- Health & Fitness
- Other
Putting Content and Privacy Restrictions in Place
This feature will allow you to prevent your child from viewing mature or explicit content in native Apple apps like iTunes or the App Store. You will also be able to set permissions to restrict them from changing the privacy settings on the iOS device.
Select Settings > Screen Time > Content & Privacy to begin. Options on this page include:
- iTunes and App Store Purchases: Restrict the ability to install/delete apps and make in-app purchases.
- Allowed Apps: Restrict the native Apple apps your child can use (Mail, Safari, FaceTime, etc).
- Content Restrictions: Restrict the content your child can access across the entire device. Generally speaking, this feature ensures that your child can’t access explicit content, such as movies or TV shows over a certain rating, explicit books or music, or explicit web content searched through Safari.
- Privacy: Restrict location services and apps that rely on user data and input.
How to Set Parental Controls with Bark
Bark is the perfect choice for blended tech families — that is, families in which a parent has an Android device and children have iPhones. Dedicated iOS families are also great candidates for Bark! We use kid-proof technology that allows parents to manage screen time and filter websites easily with little fuss. Setting healthy boundaries around tech use is crucial as kids grow up, and Bark provides unparalleled customization not only for each family but for each individual child.
Screen time features you won’t find anywhere else
Bark’s approach to screen time centers on the idea that different times of day call for different screen time rules — one size definitely doesn’t fit all. For example, when your kids are in school, you can block access to everything but educational sites. And at bedtime, you can allow apps to help them wind down for the evening. And because all kids deserve to blow off a little steam, you can designate free time hours just for play.
Check out our step-by-step guide to setting up screen time schedules with the Bark app.
Web filtering as unique as your family
Our world-class web filter lets you select exactly which websites your child can access on their devices. You can allow or block specific sites — or even whole categories like streaming services, online gaming, sexual content, and more. You can also decide exactly which apps (especially potentially dangerous ones like Snapchat or Omegle) your child can access and when.
**This blog post was updated on December 7, 2023.**
Androids make great first phones for kids, and there are lots of models for families to choose from. No matter which one you go with, it’s important that you help keep your kids safe while they’re texting, playing games, and surfing the web. In this post, we’ll walk you through how to use two of the best Android parental control apps on the market. Google Family Link is a great free app for basic online safety, while Bark (that’s us!) is a premium, all-in-one safety solution that provides comprehensive protection for families.
Using Google Family Link for Android Parental Controls
Devices like Pixels, Galaxies, and Palms have limited built-in controls. Fortunately, Google Family Link provides a robust set of parental controls — think of it as a free safety companion app for Android devices. It allows you to view your child’s online activity, manage their apps, set screen time limits, and more. Parents with iOS devices can even use it, making it perfect for mixed-device households. We have an entire guide to Family Link with step-by-step instructions for all kinds of parental controls, but we’ve highlighted the most important ones to get you started.
How to Get Family Link Set Up
- Download the free Family Link app onto your own device (Android or iPhone).
- If your child already has a Google account, Family Link will walk you through linking both of your accounts.
- If your child doesn’t already have a Google account (or Gmail), you’ll need to create one for your child so that you can use Family Link.
- Once complete, children can sign in to their device with the new account.
- Once the accounts are linked, use Family Link to set digital ground rules for your family.
How to Manage Your Child's Chrome Web Browsing
- Open the Family Link app.
- Select your child.
- Tap Content Restricitons.
- Tap Google Chrome.
- Choose the setting that’s right for your family:
- Allow all sites: Your child can visit all sites except the ones you block.
- Try to block explicit sites: No filter is perfect, but this should help hide sexually explicit and violent sites.
- Only allow certain sites: Your child will only be able to visit the sites you allow.
- Tap Manage sites to manually allow or block certain sites.
How to Turn on YouTube Restricted Mode
- Open the Family Link app.
- Select your child.
- Tap Content Restrictions.
- Tap YouTube.
- Enable Restricted Mode.
How to View Your Child’s Android Activity
- Open the Family Link app.
- Select your child.
- Tap Highlights.
Bark’s Android Parental Control Features
At Bark, we use kid-proof technology that allows families to manage screen time and block websites easily with just the tap of a button. Setting healthy boundaries around tech use is crucial as kids grow up, and Bark provides customization not only for each family but for each child. You can put Bark’s parental control app on any Android, or you can also purchase a Bark Phone, which is an Android that comes with Bark’s software built in.
Dynamic screen time schedules
Bark’s approach to screen time centers on the idea that different times of day call for different screen time rules — one size definitely doesn’t fit all. For example, when your kids are in school, you can block access to everything but educational sites. And at bedtime, you can allow apps to help them wind down for the evening. And because all kids deserve to blow off a little steam, you can designate free time hours just for play.
- Check out our step-by-step guide to setting up screen time schedules with the Bark app.
App & web blocking
Our robust web filter lets you select exactly which websites your child can access on their devices. You can allow or block specific sites — or even whole categories like streaming services, online gaming, sexual content, and more. You can also decide exactly which apps your child can access and when.
- Learn how to set up filtering rules with the Bark app.
How to block an app or site using Bark
- From your dashboard, find your child’s profile.
- Select Settings.
- Choose Parental controls.
- Review the rule sets you’ve scheduled.
- Scroll down until you see Screen time rule sets and select the rule set currently applied.
- Toggle the app or site to Blocked.
- Repeat these steps for any other screen time rule sets you’ve scheduled.
- You’re all set!
Content monitoring
Blocking and screen time scheduling are great ways to prevent access to inappropriate content, but what about protection on the apps and platforms your child is allowed to use? That’s where monitoring comes in. Bark scans your kid’s text messages and social media activity for signs of bullying, suicidal ideation, online predators, and more. If something concerning is found, you’ll get an alert so you can check in and make sure everything’s okay.
- Read more about what Bark monitors.

It seems every few weeks a new app emerges that allows for anonymous commenting on other user's posts. These apps do not necessarily require a user profile or a connection to an identity in order to make comments. No one holds cyberbullies and trolls are accountable for their behavior. With no accountability for user actions, these apps are rife with anonymous cyberbullying, sexual predators, and other online issues. Not all comments are mean or harmful, but in general, anonymous commenting apps promote a lack of responsibility for users. Such apps allow people to say hurtful and sometimes downright hateful messages without being identified. This happens more with apps that do not have moderators.
Why Anonymous Commenting Apps Are Harmful
Our role as adults is to teach our kids to be positive digital citizens, this includes talking to them about anonymous commenting apps. It is important to ask our kids if they are using such apps, and explain why these kinds of apps can contribute to a negative online culture. When an app is used to cyberbully others, even if we are not the ones participating, we need to ask ourselves if we should even use and promote the app.
Anonymous commenting apps also go against online safety procedures. One way to be safe online is to never communicate with someone you don't know. If you don't know who is commenting, then you don't know with whom you are communicating. Only communicating with people that you know should be part of your technology contract. If you haven't already done so, it might be beneficial to review the contract and update your family's rules on anonymous commenting apps.
The latest in a string of anonymous posting apps is Sarahah.com, which integrates with both Snapchat and Instagram. Originally created as a way for employees to provide frank feedback to their employers, the developers soon saw an opportunity for a different market. They began marketing the app as a way for friends to connect and "[i]mprove your friendship by discovering your strengths and areas for improvement."
Let's be honest, with an underdeveloped frontal cortex lobe which results in impulse control issues, most kids and teens (and yes, even some adults) have impulse control issues and may not be able to offer constructive criticism in order to help others work on areas of improvement. Apps like this do not generally result in positive or constructive comments to help one another; they tend to result in insults, racial remarks, and cyberbullying.
4 Articles on the Top-Selling App and Why It Leads to Anonymous Cyberbullying
Mashable: How an App You've Never Heard of Became the Most Popular iPhone App in the World
Independent: Sarahah: The Top iPhone App in the World is Being Used to Bully People, Users Claim
Inverse: Is Sarahah Doomed to Devolve Into Bullying and Hate
Business Insider: The Top Free App in the App Store Right Now is Being Called "a Breeding Ground for Hate"
This app is cause for concern and is included on our risky app list. Bark parents are notified when your kids have downloaded it to their phone or if they ever do. Sarahah's integration with Snapchat, a site that deletes posts after they have been seen, and Instagram, a place one study reports teenagers claim is the site where they experience the most cyberbullying, is a bit alarming. Further, the cyberbulling allegations are real. We have seen cyberbullying with the Sarahah/Snapchat integration actually happen.
First, talk to your kids about using anonymous commenting apps, or rather the reasons you don't want them to use these kinds of apps. Then sign them up for Sign up for Bark today and get alerts on any potential anonymous cyberbullying or other online issues your child is facing.

Roasting is a term from comedy where a comedian roasts another person with good humor, but now also encompasses online roasting of individuals as a new type of cyberbullying.
The trend started on Reddit, where users would post pictures of themselves holding up a sign saying “Roast Me,” consenting to the satire. But it has now expanded to other social media sites like Facebook, Whatsapp, and Snapchat. And the big difference is that this is usually done without the consent or desire of the individual to be roasted.
Initially, roasting can start out innocuous and light-hearted; however, that is not where it always ends. Teens of all ages and genders are participating in the new trend. But a recent study points to research showing that girls are more likely to cyberbully and be bullied online, including roasting. Below are a few ways to discuss roasting with your child and how to know if it has moved from banter to bullying.
Understanding The Different Types of Cyberbullying: Encouraging Communication
Open up a dialogue about bullying, cyberbullying and roasting. Ask open ended, but specific, questions about these topics. For example: “Have you heard about roasting online?” “Have you ever experienced roasting or participated in roasting someone else?” "If so, what was the experience like?” This kind of dialogue demonstrates that you are open to listening to what your child has to say on the subject and that they can come talk to you about it.
Some children are afraid to come forward about being roasted, even when it has moved into bullying. This is because they don’t want to be seen as someone who can’t take a joke. You can explain that humiliating, harsh criticism is not roasting — it is bullying. If the roasting has moved from something silly to something hurtful, then it’s no longer a joke and it’s okay to ask a trusted adult for help. Validate their feelings and together come up with a solution on how to respond to the bullying. Recommend solutions that revolve around consent, being a responsible digital citizen, and using empathy when faced with tough situations.
Talk About Consent
While Reddit may not be the best model for social behavior, the original postings were Redditors who consented to the roasts. However, now that roasting has spread to other social media platforms this is not always the case. Discussions about consent in this context can help your child understand when roasting turns to bullying.
One thing to remind your children is that “yes” is not a forever and always word. Just because someone has initially consented to some silly joking around doesn’t mean they have consented to more than that. And even if they did initially consent, they can say no later. Respecting whether or not someone has consented to protracted banter is part of being a smart digital citizen. Online responsibility includes checking in and making sure people are still okay with how the conversation is going.
Digital Citizenship and Empathy
One way to be a responsible digital citizen is to employ empathy in communications online. Talk to your child about what empathy means, have a discussion about what being kind and compassionate looks like. Ask them, “If you were in the other person’s shoes how would you feel about the things that are being said?” Or remind them that if they wouldn’t say it to someone’s face, they should not say it on social media. It's important for kids to understand this concept, even if they are using sites where posts are anonymous. Everyone has a responsibility to be a positive influencer in their group by being courteous and respectful in communications. This is true even when it’s a group text among friends.
Remind your children that it is okay to have fun with their friends through social media, but to think about their actions and to not have fun at another person’s expense. An open dialogue that focuses on consent and empathy can help your child navigate social media with an intent to have positive interactions. Bark can be part of this discussion! Explain that we’re a tool that helps keep them safe online and alerts you to potential types of cyberbullying and online predators. Our alerts also provide expert advice on finding solutions to these issues.